In this section, we will talk about server-side attacks.
Server-side attacks don't require user interaction.
These attacks can be used with the web servers.
We can also use them against a normal computer that people use every day.
To do these attacks, we are going to be targeting our Metasploitable device.
The reason why we are going to be using it against our Melasploitable device is that if our target uses a personal computer, and if they are not on the same network as us, then even if we manage to get their IP address, their IP address is going to be behind a router.
They will probably be connecting through a router, and therefore, if we use the IP to try and determine what applications are installed and what operating system run on it, we will not get much useful information because we are only going to be getting information about the router and not about the person.
The person will be hiding behind the router.
When we are targeting a web server, then the server will have an IP address, and we can access that IP address directly on the internet.
This attack will work if the person has a real IP and if the person is on the same network.
If we can ping the person, even if it's a personal computer, then we can run all of the attacks and all of the information-gathering methods that we're going to learn about.
We are going to be targeting our Metasploitable device.
Before we start working on it, we will just check the network settings.
Just to verify it, it is set to NAT, and it is on the same network as the Kali machine.
This Kali machine is going to be our attacking machine.
If we do ifconfig on the Metasploitable machine, we will be able to see the IP address of it as shown in the following screenshot:
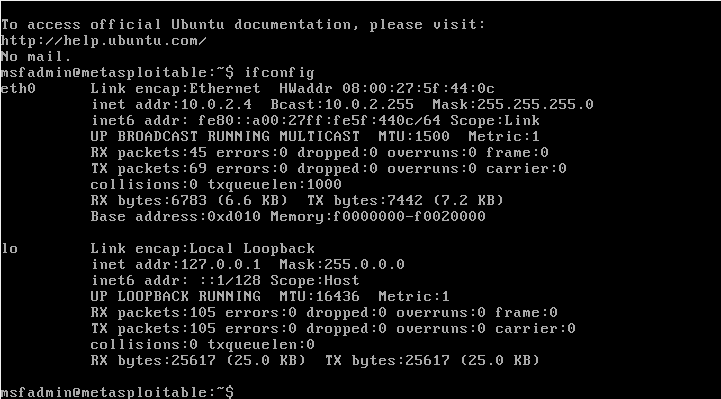
In the above screenshot, we can see that 10.0.2.4 is the IP of Metasploitable device.
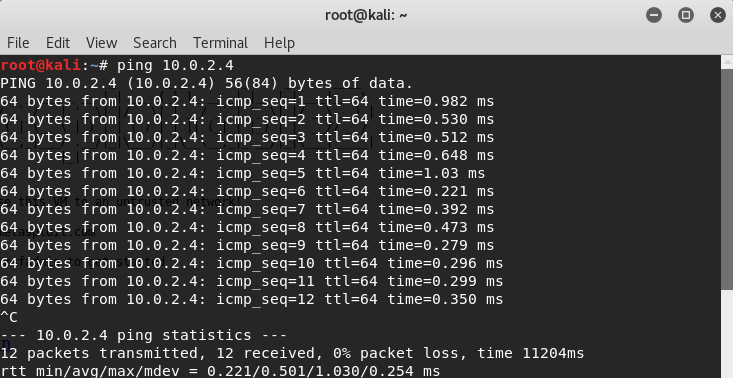
Now, if we go to Kali machine, we should be able to ping it.
In the following screenshot, we can see that when we ping on the IP, we are getting responses back from the machine.
Now, we can try and test its security as shown with the next screenshot:
Again, we can use these attacks and these approaches against any computer that we can ping.
Server-side attacks work against a normal computer, websites, web servers, people, as long as we can ping them.
Just to convey this idea, we will see the Metasploitable machine.
It is just a normal virtual machine that we can use right here to do anything we want.
Using the -ls command, we can list it, and we can even install a graphical interface.
Then we will be able to use it in the way we use in Kali machine.
But it has a web server.
If we try to navigate to the server, we will see that it has websites that we can actually read and browse.
We're going to have a look at these websites and see how we can pen test them in the later chapters as we can see in the following screenshot:
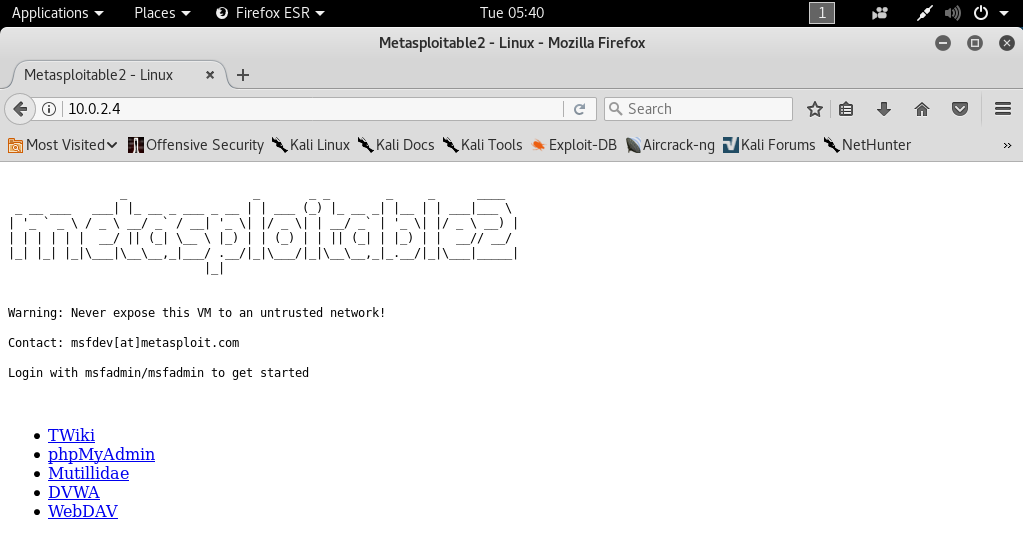
Everything is a computer, and if we can ping the IP, we can use server-side attacks.
These attacks mostly work against server because server always has real IPs.
If the person is in the same network as we are, then we can ping them to do all of these attacks as well.
Sem comentários:
Enviar um comentário