Fake authentication attack
In the previous section, we saw how easy it is to crack a WEP key on a busy network.
In a busy network, the number of data increases very fast.
One problem that we could face is if the network is not busy.
If the network is not busy, the number of data will be increasing very very slowly.
At that time we're going to fake as an AP that doesn't have any clients connected to it or an AP that has a client connected to it, but the client is not using the network as heavily as the client in the previous section.
Let's look at an example.
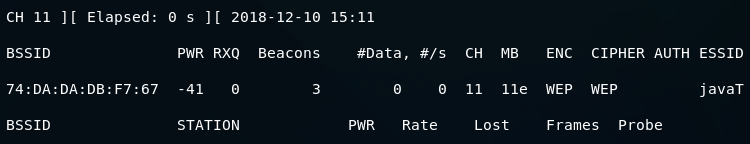
We will run airodump against the target AP which is our.
We now have our, the same AP that we used before, but the difference is that we've disconnected the clients that were connected to do this attack.
As we can see, in the client area, there are no clients connected and the #Data is 0, it didn't even go to 1.
In this section, we want to be able to crack a key like this, with 0 data:
To solve this problem, what we can do is inject packets into the traffic.
When we do this, we can force the AP to create a new packet with the new IVs in them, and then capture these IVs.
But we have to authenticate our device with the target AP before we can inject packets. APs have lists of all of the devices that are connected to them.
They can ignore any packets that come from a device that is not connected.
If a device that doesn't have the key tries to send a packet to the router, the router will just ignore the packet, and it wouldn't even try to see what's inside it.
Before we can inject packets into a router, we have to authenticate ourselves with the router.
To do this, we're going to use a method called fake authentication.
In the previous section, we already executed airodump.
Let's see how we can use fake authentication.
In the previous screenshot, we can see that AUTH have no value.
Once we have done fake authentication, we will see an OPN show up there, which will mean that we have successfully falsely authenticated our device with the target AP. We will use the following command to do that:
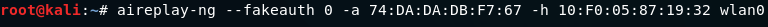
With aireplay-ng, we're going to use a --fakeauth attack.
In this attack, we include the type of attack and the number of packets that we want to send, which is --fakeauth 0. We are going to use -a, to include the target network which is 74:DA:DA:DB:F7:67.
Then we're going to use -h, to include our MAC address.
To get our MAC address, we are going to run the ifconfig wlan0command:

Here, wlan0 is the name of our Wi-Fi card.
With aireplay-ng, the type of attack that we're trying to do, we're trying to perform a fake authentication attack, to authenticate our MAC address so that we can inject packets into the target network.
We will send 0 which means do it once, then -a with the MAC address of the access point(AP), then -h with the MAC address of the device that we want to perform a fake authentication to, and then wlan0, the name of the WiFi card in monitor mode.
Now we hit Enter:
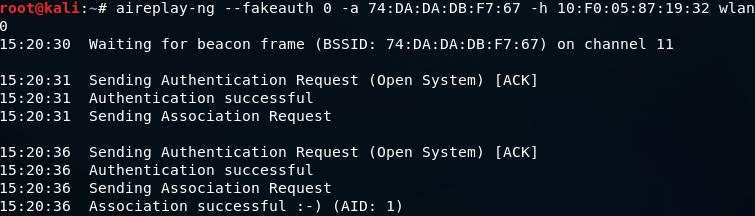
In the above image, we can see that -a sent an authentication request, and it was successful.
The network becomes an open network, and our client showed up as if it was a client connected to the network.
We're not actually connected, but we are authenticated with the network and have an association with it so that we can inject packets into the AP.
It will now receive any request that we send to it.
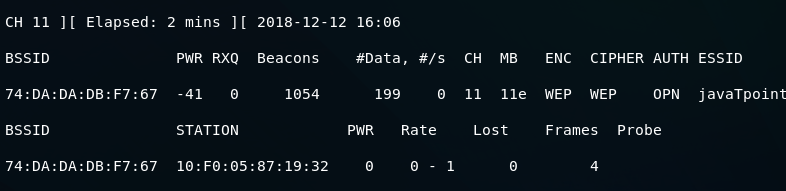
Following is the output:
Sem comentários:
Enviar um comentário